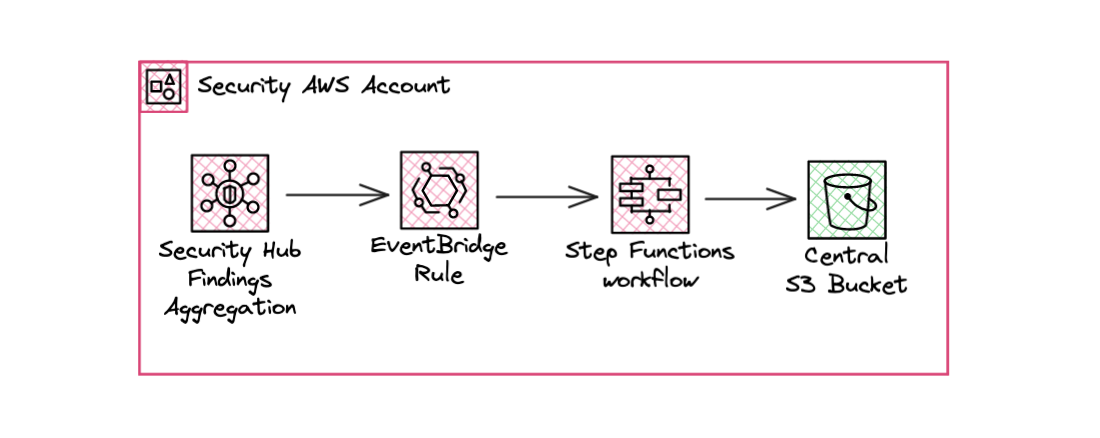
Export all Security Hub findings to S3
AWS Security Hub allows security teams to centralize most of the findings from AWS services but does not provide a native feature to exporting them in a S3 bucket, like CloudTrail or GuardDuty do. I’m surprised by this lack of native export. AWS already shares several solutions to export them in a CSV file on-demand, on-schedule or the whole finding history one-shot. But in the end, I had to find a solution to export them in near real-time to an S3 bucket so that they could be integrated into a third-party SIEM solution. ...
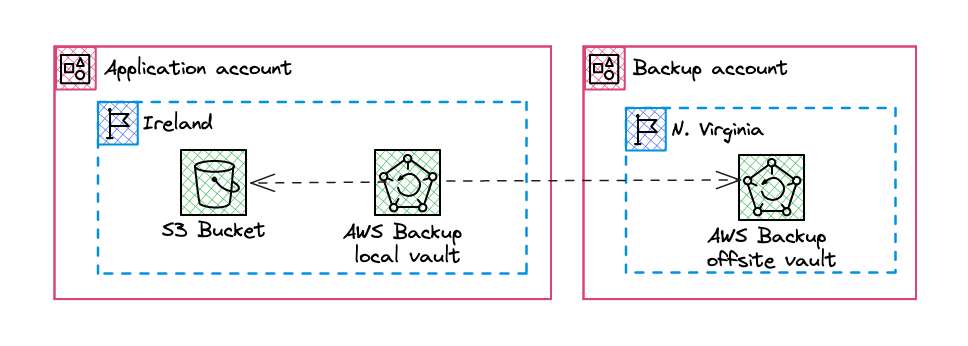
Some tips on deploying AWS Backup
The purpose of this article is to share some technical issues I encountered and how to avoid them when deploying the AWS Backup managed service using the “3-2-1” backup rule (at least, to get closer). There will be no advice on backup strategies, RPO/RTO, or an introduction to or start with configuring the AWS Backup service. On these uncovered topics, I suggest you take a look at the impressive list of over 40 AWS articles; I also added a few other AWS publications that are not referenced on their own list… ...
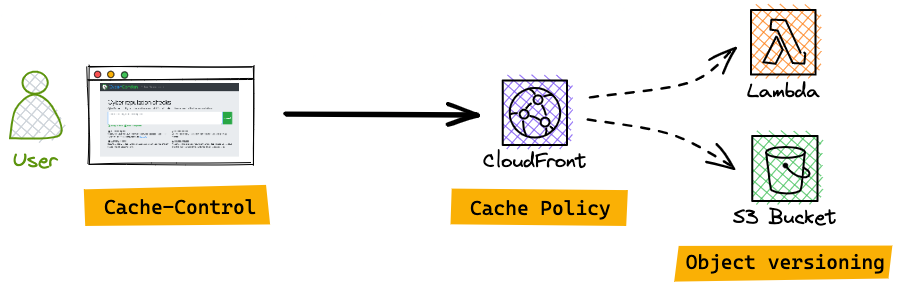
CyberGordon - CDN cache optimization
Web cache introduction A Web cache is a system for optimizing the Web page loads. It is implemented both client-side (browser) and server-side (Content Delivery Network (CDN)/Web server). Web cache optimization brings several benefits: On the user side, the web page is displayed faster; very useful during mobile browsing. :racehorse: On the server side, the load is lower, and with the cloud model of pay-as-you-go, this results in cost reductions. :moneybag: And you reduce your carbon footprint by eliminating many unnecessary requests processed by browsers and servers. :seedling: The context of my project CyberGordon website static resources (images, css, js, json) are hosted on a AWS S3 Bucket behind AWS CloudFront (CDN). You can have a presentation of the architecture on my specific blog post. ...
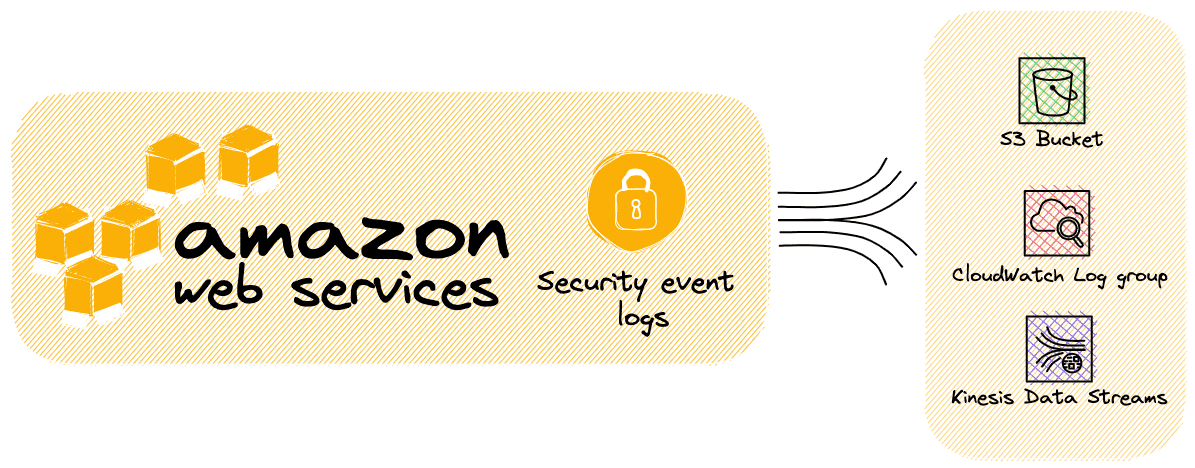
AWS services security event logs - A Reference
This post is always in progress This blog post was initially written on 2021 and AWS continues to add features continuously. If you notice something wrong or obsolete, share it to me! Why this repository AWS lets customers to generate and integrate some services security logs. However, each log source has its own configuration making understanding quite difficult for new customers. This post references main AWS services logging sources with its properties, format(s), some examples and resource to go further. ...
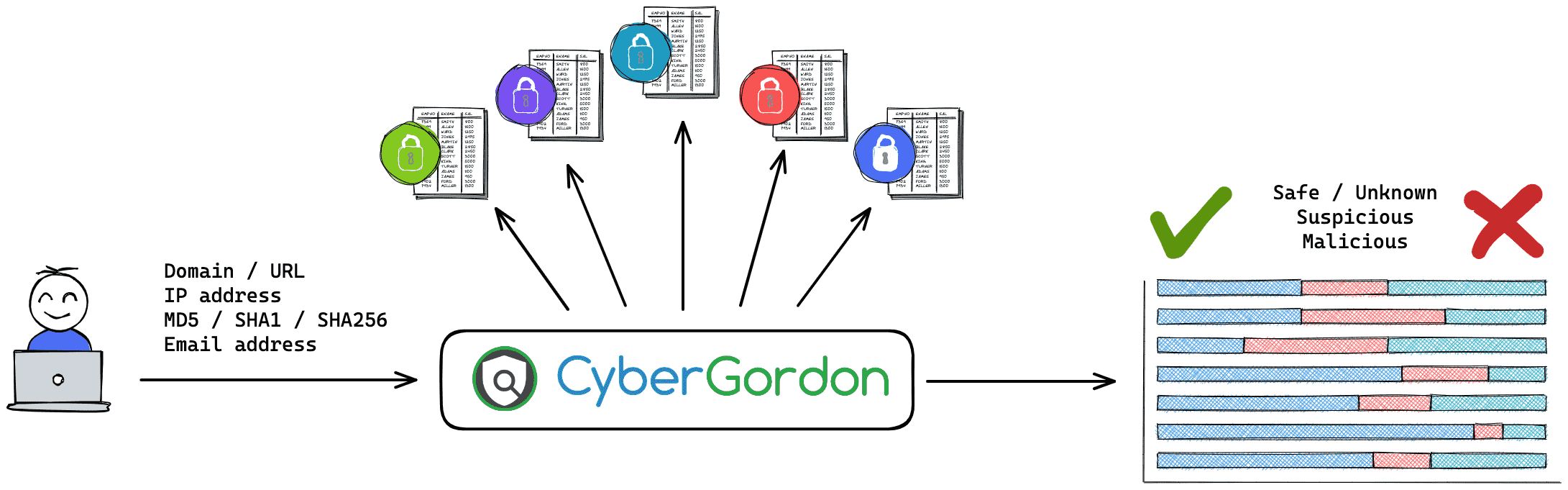
The genesis and architecture of my CyberGordon project
Quick introduction CyberGordon quickly provides you threat and risk information about observables such as IP addresses or domain names by querying multiple threat intelligence sources. Thanks to each source that provides free access to great Threat Intelligence against phishing and malware. Without them, CyberGordon would have not been there. Why CyberGordon ? Whether it be during my investigations at work or personal surfing sessions, I’m too lazy to use several sources to check if a domain or email address is suspicious or malicious. Some awesome OSINT tools exist, but I didn’t have one to aggregates them all into one simple web interface. On top of that, I wanted to start by building a usable and useful tool on AWS infrastructure that I could share with my entourage. I would have liked to share CyberGordon widely, but I’m constrained by the query limits that free API sources provide. Lastly, the lock down during the COVID-19 crisis gave me a lot of time, a rare resource that considerably contributed in completing CyberGordon. ...